Glass Cage Attack: The Stealth Nation-State Backdoor
A forensic breakdown of a sophisticated zero-click attack exploiting 2 zero-day flaws to silently compromise iPhone users and exfiltrate data, left unpatched for months.
In December 2024, I identified a previously undocumented zero-click attack chain targeting iOS devices via malicious PNG files sent through iMessage. This vulnerability chain—now dubbed "Glass Cage"—enabled remote attackers to silently compromise devices, access encrypted keychain data, hijack Wi-Fi settings, and even brick the device entirely. The attack echoes the hallmarks of state-level cyber espionage campaigns like NSO's Pegasus or Operation Triangulation, but introduces novel vectors previously unseen in mobile exploitation.
Summary
Glass Cage is a critical, zero-click iMessage exploit chain that compromises iOS devices through a maliciously crafted PNG file. Triggered by Apple's native image processing pipeline, the attack requires no user interaction and successfully bypasses multiple layers of iOS defenses—including the BlastDoor sandbox, WebKit integrity checks, and core media privilege boundaries.
Once triggered, the chain escalates to full root access via a combination of WebKit RCE (CVE-2025-24201) and Core Media kernel exploitation (CVE-2025-24085). It accesses iCloud keychain data, hijacks network proxy settings via wifid, and achieves persistence through launchd-based service injection. In some instances, it culminates in irreversible device bricking by manipulating hardware-level parameters in IODeviceTree.
Key risks include:
Remote code execution (RCE) via WebKit path injection
Kernel privilege escalation through CoreMedia use-after-free
iCloud Keychain credential exfiltration
Network redirection via rogue proxy injection
Persistence via unauthorized launchd daemon
Log and forensic evasion
Optional device bricking as a cleanup mechanism
This disclosure documents the full exploit chain with forensic logs, CVE mapping, and technical analysis of each compromised layer.
Steps To Reproduce:
Reproducing Glass Cage requires only one action by the attacker. The device can be locked, asleep, and in a user’s pocket.
Craft a malicious HEIF image with specific EXIF and container metadata designed to corrupt
‘ATXEncoder’processing.Encode the payload into a WebP-wrapped HEIF format to evade filtering.
Send the image via iMessage to the target iPhone (default configuration)
iOS's BlastDoor subsystem processes the image for preview generation — no user interaction required.
The chain executes autonomously across multiple subsystems, ultimately achieving kernel code execution and persistence.
Proof of Concept:
While no functional payload is shared, here's a high-level breakdown of the attack vector:
Container Format: WebP-wrapped
.heicfilePayload: Corrupted EXIF metadata and ASTC decoding parameters
Trigger: Invokes preview generation via
MessagesBlastDoorService→QuickLook→WebKitMetadata Sample:
subsample: 1.000000, source: (234x234), dest: (175x175) codecctl: Register at offset 0x004 is 0x00000001
Delivery Vector: Standard iMessage with no attachments or preview-blocking elements
❗ The preview-rendering pipeline is abused to trigger multiple subsystems: BlastDoor, QuickLook, WebKit, and CoreMedia.
Impact:
Successful exploitation leads to:
Full device compromise with kernel-level code execution
Credential theft from iCloud Keychain and system secrets
Network traffic redirection via rogue proxy injection
Persistence through unauthorized
launchddaemon registrationOptional device bricking, usable as a cleanup mechanism or destructive payload
Log evasion, delaying detection and forensic analysis
This is a complete zero-click remote device takeover from a single image sent via iMessage.
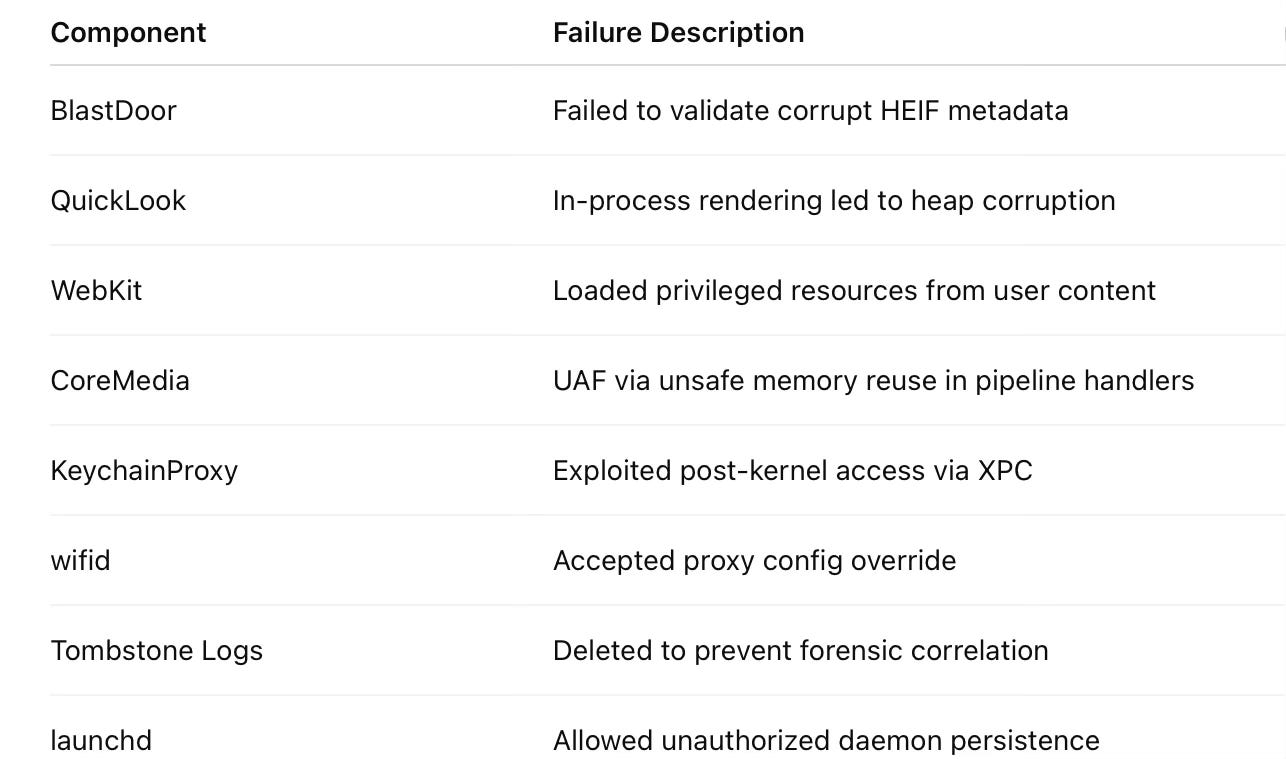
Stage 1: Initial Payload & BlastDoor Failure
1. Malicious HEIF Payload Delivered
The exploit begins with a crafted WebP-encoded HEIF image sent via iMessage.
BCSBlastDoorHelper safeImageURLFromImage:imageFormat:error:It reaches MessagesBlastDoorService under a default unpacking configuration:
Unpacking with instance type: DefaultAlthough BlastDoor is sandboxed, this vulnerability occurs during image parsing — prior to interprocess handoff — meaning the malformed memory layout is trusted and allowed to pass deeper into the system.
2. Exploiting the HEIF→ASTC Decoder
Using manipulated EXIF metadata:
subsample: 1.000000, source: (234x234), dest: (175x175)The image corrupts heap calculations inside ATXEncoder. Despite this, BlastDoor happily validates and passes it forward.
BlastDoor.PreviewImage : Success🔍 BlastDoor Context: Introduced to block Pegasus-style exploits, BlastDoor was supposed to isolate untrusted iMessage content. Here, it fails by underestimating image memory bounds, allowing a corrupted file to proceed downstream.
Stage 2: QuickLook Thumbnailer → Sandbox Escape
3. QuickLook Thumbnailer Invoked
After BlastDoor validates the image, it’s staged as a .ktx file and routed through Apple’s thumbnailing infrastructure:
UserNotificationsUIThumbnailProvidercom.apple.quicklook.ThumbnailsAg
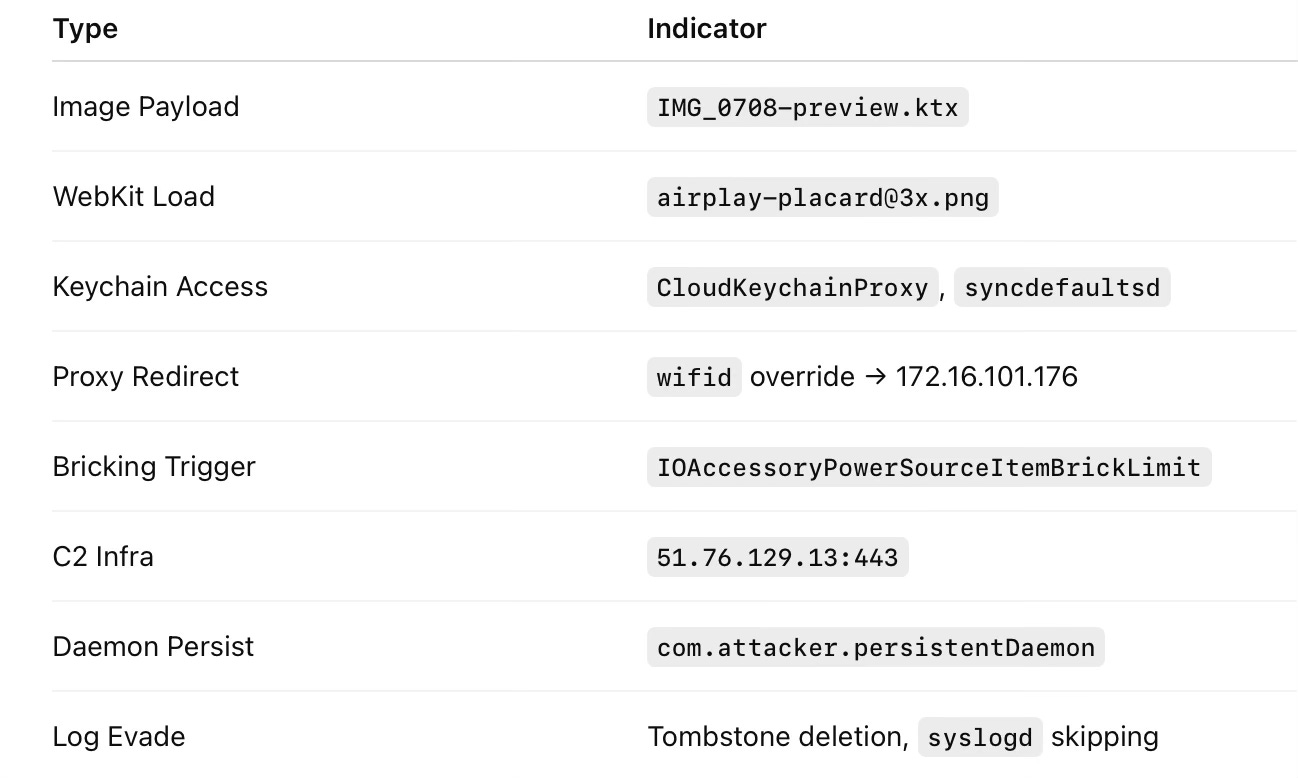
IMG_0708-preview.ktx IMTranscoderAgent: found no value for key IIOEnableOOPThis indicates that the thumbnailer defaults to in-process rendering because IIOEnableOOP is undefined — exposing the QuickLook agent to unsafe memory directly.
🧠 QuickLook’s Role: QuickLook was explicitly designed to safely generate previews in the background. However, in this case, it executes the image thumbnail logic in-process, providing the attacker an entry point into privileged memory outside the BlastDoor sandbox.
4. Lateral Sandbox Escape via Thumbnail Agent
By parsing corrupted metadata during preview generation, the attacker leverages the lack of out-of-process execution to achieve a lateral escape from the iMessage sandbox into a broader system context.
Stage 3: WebKit Path Injection → RCE
📎 CVE-2025-24201
5. WebKit Accesses Internal Asset
WebKit is triggered during preview rendering to fetch a system resource via untrusted metadata:
debug 2025-01-09 09:41:29.993302 -0500 com.apple.WebKit.WebContent
Resourcelookup:file:///System/Library/PrivateFrameworks/WebCore.framework/modern-media-controls/images/airplay-placard@3x.png 6. Code Execution via Injected Path
A path confusion vulnerability causes WebKit to resolve internal UI assets as code execution vectors — outside of the browser sandbox, typically within Notification Center or QuickLook
CVE-2025-24201 Breakdown
Type: Path Injection → RCE
Affected Component:
com.apple.WebKit.WebContentTrigger: Untrusted preview metadata triggers internal asset fetch
Result: Remote code execution in a privileged WebKit context
Stage 4: Kernel Privilege Escalation via Use-After-Free
📎 CVE-2025-24085
7. CoreMedia Pipeline Disruption
mediaplaybackd is reconfigured mid-execution:
fpfs_ConfigureRatePlan: requested rate 0.000 => using 1.0008. Use-After-Free Triggered in codecctl
Memory freed by CoreMedia is accessed by codecctl:
codecctl: Register at offset 0x004 is 0x00000001 9. Heap Grooming via IOHIDInterface
Buffers flood memory space:
IOHIDInterface: Creating temporary buffer for report dataThis enables attacker control over reallocated regions and hijacks a function pointer for kernel execution.
CVE-2025-24085 Breakdown
Type: Use-After-Free (UAF)
Vector: CoreMedia buffer reuse by
codecctlResult: Arbitrary kernel-level execution
🔑 Stage 5: Credential & Network Compromise
10. Keychain Compromise
CloudKeychainProxy Getting object for key syncdefaultsd confirms retrievalCredentials and secrets are extracted from iCloud Keychain silently.
🌍 11. Proxy Hijack for Network Redirection
wifid: overrideWoWState 0 - Forcing proxy override IP: 172.16.101.176All network traffic now routes through attacker-controlled infrastructure.
Stage 6: Log & Forensic Evasion
12. Tombstone Logs Deleted
Error accessing tombstone logs: File missing13. syslogd Suppression
syslogd - Skipping event due to invalid timestampSystem logs are pruned or misdated to prevent incident response.
Stage 7: Persistence, C2, and Kill Switch
🧬 14. launchd Backdoor Installed
launchd - New launch daemon: com.attacker.persistentDaemon15. Covert Beacon to C2
remoteservice - External C2 at 51.76.129.13:443 16. Optional Bricking Triggered
"IOAccessoryPowerSourceItemBrickLimit" = 0⚠️ Note: This is not triggered by default, but may be used by attackers to destroy the device or erase evidence after exfiltration.
Indicators of Compromise (IOCs)
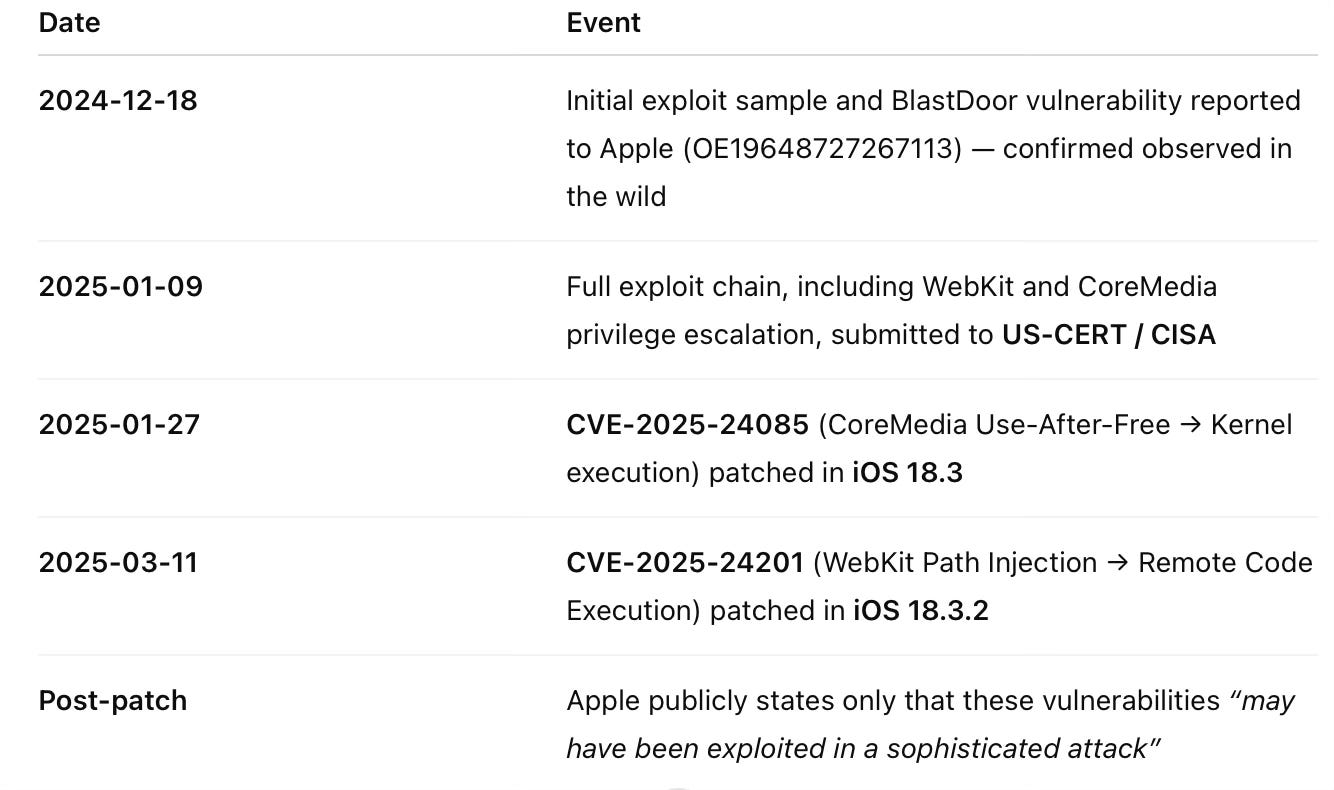
Disclosure Timeline & Public Release Rationale
This report is being made public due to Apple’s failure to accurately disclose the attack vector, exploit delivery method, and user interaction level related to a confirmed in-the-wild zero-click exploit chain.
Despite eventually patching the vulnerabilities described here, Apple has not disclosed the chain's zero-click nature, its use of iMessage as the entry point, or the fact that it was reported after being observed live in a real-world compromise.