The Crypto Heist Apple Kept Quiet: An iMessage Zero-Day in iOS 18
Between Dec 2024 and Apr 2025, an iMessage exploit let attackers hijack iPhones, steal crypto keys, and impersonate users — all triggered by receiving a malicious audio file.
A forensic walkthrough of a wormable iMessage exploit chain in iOS 18.4 enabling full device compromise.
Executive Summary
A maliciously crafted MP4 audio file, when delivered via iMessage, it triggers a high-reliability remote exploit chain in iOS 18.2 through 18.4. The chain culminates in:
Sandbox escape
Heap corruption in CoreAudio
Kernel-level privilege escalation
Wireless mesh propagation (worming)
Cryptographic identity impersonation
No user interaction is required. The exploit uses only native system APIs and entitlements, and functions on non-jailbroken devices.
🧬 Exploit Chain and API Instrumentation
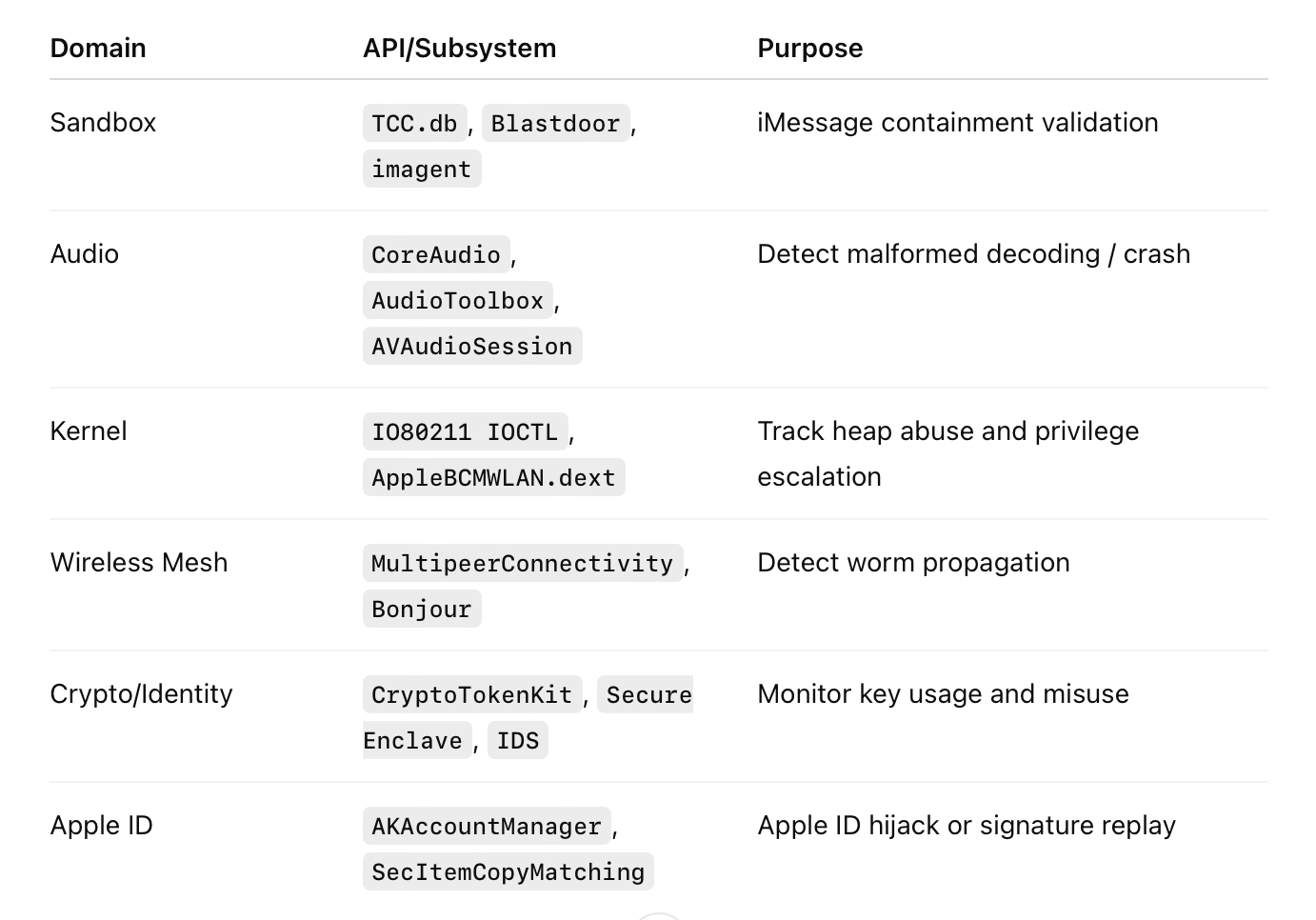
Stage 1: iMessage Blastdoor Bypass
Trigger: Audio file received from a known sender via iMessage
Components:
IDSDaemon,imagent,BlastdoorAPI Gaps:
TCC.db,SecItemCopyMatching,com.apple.imagentlogs
Log Evidence:
Blastdoor filtering: disabled due to trusted sender Blackhole spam filtering: OFFStage 2: Heap Corruption via AAC Decoding
Trigger: Malformed MP4 audio stream
Components: CoreAudio, AudioToolbox.framework
API Observables:
AVAudioSession,audiomxd,AVHapticServerInstance, PME signaling
Logs:
AVAudioSessionRouteChangeReasonUnknown inMagicCookie=0x0, inMagicCookieByteSize=39Stage 3: Kernel Escalation via Wi-Fi Driver Exploit
Trigger: Malformed AMPDU frame metadata
Components: AppleBCMWLAN.dext, IO80211Controller
API Coverage: IOCTL_APPLE80211_IOC_*, IOServiceOpen, launchd, panic-full
Logs:
setAMPDUstat unhandled kAMPDUStat_ type 13, 14 EXTERNAL: Get type=<APPLE80211_IOC_SSID> res=<FAIL>Stage 4: Peer Injection for Worming
Trigger: GAS Table poisoning
Components: identityservicesd, DBCache, PeerLookup_SwiftData
APIs: MultipeerConnectivity.framework, Bonjour, NEHotspotHelper, NWConnection
Logs:
Peer token registered: service: com.apple.madrid DBCache hit for forged URIStage 5: Key Misuse via CryptoTokenKit
Trigger: Signature reuse across system contexts
Components: CryptoTokenKit, Secure Enclave, IDSAccountService
APIs: TKTokenSession, SecKeyCreateSignature, AKAccountManager, secd
Logs:
CryptoTokenKit operation: ECDSA:digest-X962:SHA256 Parsed private key: <sepk:p256(d)> used by identityservicesd📈 API Telemetry Summary
📅 Responsible Disclosure Timeline
December 20, 2024
Initial discovery of the working exploit chain on iOS 18.2.
Reported to Apple Product Security under Report ID OE19648805943313.January 21, 2025
Report submitted to US-CERT / CISA.
Tracking ID: VRF#25-01-MPVDT.April 11, 2025
Full technical report submitted to Google Project Zero and re-escalated to Apple.April 16, 2025
Apple released iOS 18.4.1, which patched the exploit chain.
Assigned CVEs:CVE-2025-31200 (CoreAudio AAC heap corruption)
CVE-2025-31201 (AppleBCMWLAN AMPDU escalation)
June 6, 2025
Public disclosure of findings and full technical analysis.
Artifact Notes
A working exploit audio file was used to reproduce this issue on iOS 18.2 and 18.4. (available to vetted researches upon request)
⚖️ Legal & Ethical Disclosure
This report is provided for educational and defensive research purposes only.
No reverse engineering or tampering beyond lawful behavior analysis was conducted.
No exploit scripts, binaries, or media are included in public distribution.
🧾 Conclusion
This report documents a full-chain, wormable, remote compromise of iOS devices via iMessage vector. The exploit leverages default frameworks, requires no elevated entitlements, and propagates via Wi-Fi-based peer discovery. It was patched under CVE-2025-31200 and CVE-2025-31201 in iOS 18.4.1 following coordinated disclosure.